Whenever you send email or browse a website, a dns lookup is made to resolve the dns name to an IP address. Without dns, the internet can’t work as humans cannot remember IP addresses. Bind stands for Berkeley Internet Domain Name and is the most popular and widely used DNS server across the globe because of its availability and scalability. We will install and configure Primary Master Bind dns server in this tutorial. This tutorial can be used for Centos / Rhel, etc.
There are three types of DNS servers:
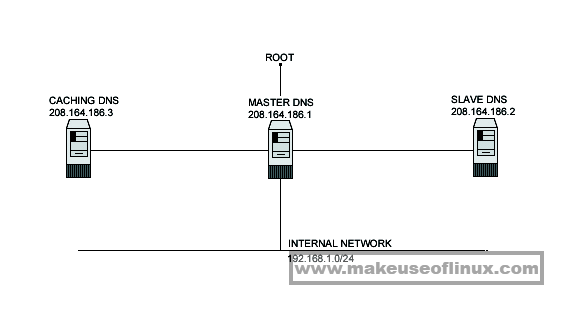
1.Caching Only DNS server
Setting up a caching only server for client local machines will reduce the load on the site’s primary server. A caching only name server will find the answer to name queries and remember the answer the next time we need it. This will shorten the waiting time the next time significantly. For security reasons, it is very important that DNS doesn’t exist between hosts on the corporate network and external hosts; it is far safer to simply use IP addresses to connect to external machines from the corporate network and vice-versa.
2. Primary Master DNS server
A primary master name server for a zone reads the data for the zone from a file on it’s host and are authoritative for that zone
3. Slave DNS server
The purpose of a slave name server is to share the load with the master server, or handle the entire load if the master server is down. A slave name server loads its data over the network from another name server usually the master name server, but it can load from another slave name server too. This process is called a zone transfer.
Install Bind DNS Server on linux
We will install bind dns server on linux, this tutorial can also be used to setup and install bind dns sever on CentOS and RHEL.
yum install bind-chroot bind-chroot x86_64 32:9.11.4-26.P2.el7_9.8 updates 93 k
Installing for dependencies:
GeoIP x86_64 1.5.0-14.el7 base 1.5 M
audit-libs-python x86_64 2.8.5-4.el7 base 76 k
bind x86_64 32:9.11.4-26.P2.el7_9.8 updates 2.3 M
bind-libs x86_64 32:9.11.4-26.P2.el7_9.8 updates 157 k
bind-libs-lite x86_64 32:9.11.4-26.P2.el7_9.8 updates 1.1 M
bind-license noarch 32:9.11.4-26.P2.el7_9.8 updates 91 k
checkpolicy x86_64 2.5-8.el7 base 295 k
geoipupdate x86_64 2.5.0-1.el7 base 35 k
libcgroup x86_64 0.41-21.el7 base 66 k
libsemanage-python x86_64 2.5-14.el7 base 113 k
policycoreutils-python x86_64 2.5-34.el7 base 457 k
python-IPy noarch 0.75-6.el7 base 32 k
python-ply noarch 3.4-11.el7 base 123 k
setools-libs x86_64 3.3.8-4.el7 base 620 k
Transaction Summary
================================================================================
Install 1 Package (+14 Dependent packages)
Total download size: 7.0 M
Installed size: 18 M
Is this ok [y/d/N]: y
Required files for dns to work
Now we need to copy named.conf template file to /var/named/chroot/etc directory
# cp /usr/share/doc/bind-9.11.4/sample/etc/named.conf /var/named/chroot/etcWe will now define our domain makeuseoflinux.com as Primary Master zone and makeuseoflinux.com.db will be the zone file containing the zone configuration. Zone file contains configuratin which does the job of name to ip address resolution.
# vi /var/named/chroot/etc/named.confoptions
{
/* make named use port 53 for the source of all queries, to allow
* firewalls to block all ports except 53:
*/
query-source port 53;
query-source-v6 port 53;
// Put files that named is allowed to write in the data/ directory:
directory "/var/named"; // the default
dump-file "data/cache_dump.db";
statistics-file "data/named_stats.txt";
memstatistics-file "data/named_mem_stats.txt";
allow-transfer {172.17.1.191;};
};
logging
{
/* If you want to enable debugging, eg. using the 'rndc trace' command,
* named will try to write the 'named.run' file in the $directory (/var/named).
* By default, SELinux policy does not allow named to modify the /var/named directory,
* so put the default debug log file in data/ :
*/
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
view "internal"
{
/* This view will contain zones you want to serve only to "internal" clients
that connect via your directly attached LAN interfaces - "localnets" .
// */
match-clients { localnets; };
match-destinations { localnets; };
recursion yes;
// all views must contain the root hints zone:
include "/etc/named.root.hints";
// include "named.rfc1912.zones";
// you should not serve your rfc1912 names to non-localhost clients.
// These are your "authoritative" internal zones, and would probably
// also be included in the "localhost_resolver" view above :
zone "makeuseoflinux.com" {
type master;
file "makeuseoflinux.com.db";
allow-update { 172.17.1.191 ; };
};
};
view "external"
{
/* This view will contain zones you want to serve only to "external" clients
* that have addresses that are not on your directly attached LAN interface subnets:
*/
match-clients { !localnets; !localhost; };
match-destinations { !localnets; !localhost; };
// match-clients { localnets; localhost; };
// match-destinations { any; };
recursion no;
// you'd probably want to deny recursion to external clients, so you don't
// end up providing free DNS service to all takers
// all views must contain the root hints zone:
include "/etc/named.root.hints";
// These are your "authoritative" external zones, and would probably
// contain entries for just your web and mail servers:
zone "makeuseoflinux.com" {
type master;
file "makeuseoflinux.com.db";
allow-update { 172.17.1.191 ; };
};
};
Important Tips
- localhost: Refers to the DNS server itself
- localnets: Refers to all the networks to which the DNS server is directly connected
- any: which is self explanatory.
Access restrictions of Bind DNS
There are two important options:
allow-query { argument; }; – allow queries for authoritative data allow-query-cache { argument; }; – allow queries for non-authoritative data (mostly cached data)
You can use address, network address or keywords “any”/”localhost”/”none” as argument
Examples:
allow-query { localhost; 10.0.0.1; 192.168.1.0/8; };
allow-query-cache { ::1; fe80::5c63:a8ff:fe2f:4526; 10.0.0.1; };
The allow-query argument will allow the servers who can query our dns server for hostname resolution.
Now lets create the zone file makeuseoflinux.com.db which should be inside /var/named/chroot/var/named
$TTL 86400
@ IN SOA ns1.makeuseoflinux.com vedkumargupta.makeuseoflinux.com (
42 ; serial (d. adams)
3H ; refresh
15M ; retry
1W ; expiry
1D ) ; minimum
IN NS ns1.makeuseoflinux.com.
IN NS ns2.makeuseoflinux.com.
IN MX 5 mail1.makeuseoflinux.com.
IN MX 10 mail2.makeuseoflinux.com.
ns1 IN A 203.90.78.86
ns2 IN A 203.90.78.86
mail1 IN A 203.90.64.183
mail2 IN A 203.90.78.86
makeuseoflinux.com. IN A 203.199.89.164
www IN CNAME makeuseoflinux.com.
ftp IN A 203.90.78.86
—————————-
Start named service and enable it, so that it can start automatically on reboot. Also verify named service status.
systemctl enable named
systemctl start named
systemctl status namedLets install dig which is used to query and check dns resolution on linux servers.
# yum install bind-utils# dig makeuseoflinux.com
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.8 <<>> makeuseoflinux.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26658
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 13
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;makeuseoflinux.com. IN A
;; ANSWER SECTION:
makeuseoflinux.com. 110 IN A 172.67.146.5
makeuseoflinux.com. 110 IN A 104.21.10.166
;; AUTHORITY SECTION:
makeuseoflinux.com. 172609 IN NS weston.ns.cloudflare.com.
makeuseoflinux.com. 172609 IN NS bristol.ns.cloudflare.com.
;; ADDITIONAL SECTION:
bristol.ns.cloudflare.com. 172609 IN A 108.162.194.47
bristol.ns.cloudflare.com. 172609 IN A 162.159.38.47
bristol.ns.cloudflare.com. 172609 IN A 172.64.34.47
weston.ns.cloudflare.com. 172609 IN A 172.64.35.138
weston.ns.cloudflare.com. 172609 IN A 108.162.195.138
weston.ns.cloudflare.com. 172609 IN A 162.159.44.138
bristol.ns.cloudflare.com. 172609 IN AAAA 2803:f800:50::6ca2:c22f
bristol.ns.cloudflare.com. 172609 IN AAAA 2a06:98c1:50::ac40:222f
bristol.ns.cloudflare.com. 172609 IN AAAA 2606:4700:50::a29f:262f
weston.ns.cloudflare.com. 172609 IN AAAA 2606:4700:58::a29f:2c8a
weston.ns.cloudflare.com. 172609 IN AAAA 2803:f800:50::6ca2:c38a
weston.ns.cloudflare.com. 172609 IN AAAA 2a06:98c1:50::ac40:238a
;; Query time: 0 msec
;; SERVER: 192.168.2.136#53(192.168.2.136)
;; WHEN: Sat Dec 18 16:16:36 IST 2021
;; MSG SIZE rcvd: 400
Let us query and see if we are also able to resolve public dns like google.com(we have set recursion to yes)
# dig google.com
; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.8 <<>> google.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27475
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 4, ADDITIONAL: 9
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;google.com. IN A
;; ANSWER SECTION:
google.com. 300 IN A 142.250.67.174
;; AUTHORITY SECTION:
google.com. 172472 IN NS ns3.google.com.
google.com. 172472 IN NS ns1.google.com.
google.com. 172472 IN NS ns2.google.com.
google.com. 172472 IN NS ns4.google.com.
;; ADDITIONAL SECTION:
ns2.google.com. 172472 IN A 216.239.34.10
ns1.google.com. 172472 IN A 216.239.32.10
ns3.google.com. 172472 IN A 216.239.36.10
ns4.google.com. 172472 IN A 216.239.38.10
ns2.google.com. 172472 IN AAAA 2001:4860:4802:34::a
ns1.google.com. 172472 IN AAAA 2001:4860:4802:32::a
ns3.google.com. 172472 IN AAAA 2001:4860:4802:36::a
ns4.google.com. 172472 IN AAAA 2001:4860:4802:38::a
;; Query time: 66 msec
;; SERVER: 192.168.2.136#53(192.168.2.136)
;; WHEN: Sat Dec 18 16:18:24 IST 2021
;; MSG SIZE rcvd: 303
Import Tips if you have Master/Slave DNS setup
- If zone transfer is not taking place on slave then check allow-transfer on master and masters ip on slave.
- If still not working then check the match-clients and match-destination options.
Conclusion
We have setup and install bind dns server successfully. We have configured domain makeuseoflinux.com for testing the functionality of our dns server. We are able to resolve makeuseoflinux.com and also public domain like google.com.

